Dirty Bird Industries Security and Fraud Mitigation
In the last year alone we’ve seen data breaches from Twitter, Marriott hotels, MGM Resorts and even Zoom, the online meeting platform trusted by companies and educational institutions around the world. Hackers and fraudsters are becoming more creative and more aggressive in their lawless behavior.
At AR15Discounts.com we take security very seriously. I’m not just a co-founder of the company, I’m also a programmer by trade and I’ve helped large companies from many industries including Energy, Agriculture, Finance and Retail deploy usable and secure websites. I’d like to tell you about what we’re doing to keep your data safe.
Our Internal Security Measures
There is no such thing as a one-stop-shop for security. Regardless of the industry, bad actors will happily utilize any number of attack vectors in order to compromise sensitive information. This is why we have a multi-layered approach to security.
1. Network Edge Protection
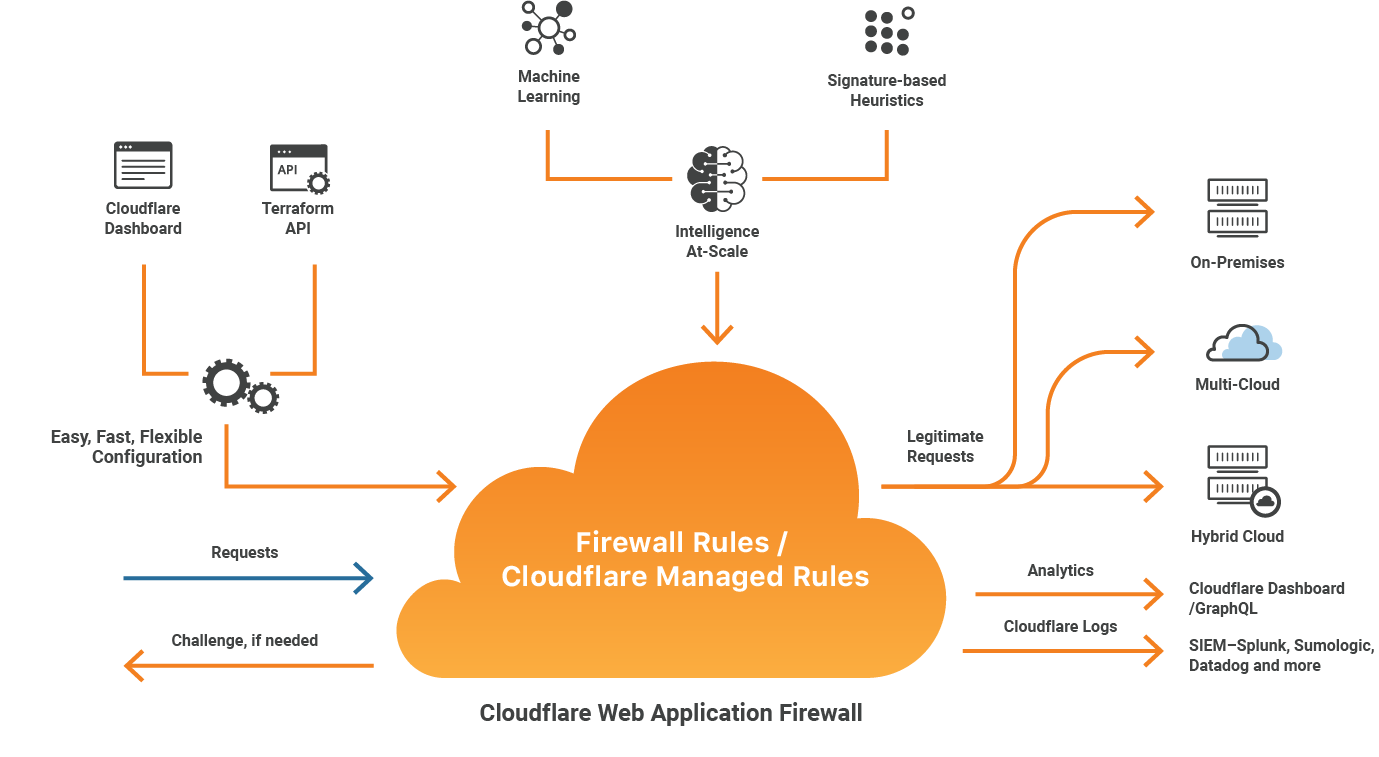
We utilize Cloudflare to manage DNS and create a barrier between our customers and bad actors before they even reach our server infrastructure. Trusted by tech giants such as IBM, Shopify and Zendesk, Cloudflare is uniquely positioned to learn from high profile attacks and quickly deploy mitigation techniques to the rest of their 58,000 customers.
Key Features:
- Deep Packet Inspection, covering applications / Layer 7 – Protection from SQL injection, cross-site scraping attacks and thousands more.
- Full stack DDoS protection
- Automated Learning > Security Driven Research > Virtual Patching – Protects against zero-day vulnerabilities or new threats with patches automatically deployed by the Cloudflare security team.
- IP Reputation Database Integration – Real-time intelligence on over 1 billion unique IPs used to block malicious traffic.
Click here to learn more about Cloudflare security.
2. Credit Card Security
This part might be the simplest. We utilize Authorize.net, one of the largest Processing Gateways in the world.
We integrate with them in a way that ensures a customers’ full credit card number never actually hits our servers. Instead, when you enter your credit card information and click “Place Order” your browser bypasses our server and connects directly and securely via 256-bit Bank Level Encryption to Authorize.net. Authorize.net processes the transaction and then gives us a unique “token” which allows us to capture the funds. Even if you choose the option to save your credit card information, all our server remembers is that token which would be useless to a fraudster even if it did get stolen. This also means that none of our employees (including myself) can gain access to your full credit card number.
Please note, just because the information never touches are server, doesn’t mean you’re completely protected by this alone. For example if your device’s browser is compromised, then your information is still vulnerable. Not to worry though, we’ve got you covered there too. You’ll learn more about this in our “Browser / Client Side Security” section.
3. Server Side Security

We host our websites with Pagely, a premier managed hosting provider touting an impressive client list including Disney, Visa and Garmin just to name a few. Since their founding in 2006 they have dedicated an incredible amount of time and money to develop PressARMOR™, their security suite which not only uses cutting edge security software but also includes how they train staff, perform outreach and research new threats.
Key Features:
- Supplemental Web Application Firewall (WAF) – Includes custom rule sets developed by Pagely which supplements the network level firewall.
- Real-time, file-system level malware scanning
- Framework specific security enhancements
- Dedicated hardware for each client
- CHROOT user separation
- 2-Factor Authentication
Click here to learn more about PressARMOR™
4. Cloudflare’s Page Shield Technology

We’re one of the few websites in our industry that uses Cloudflare’s Page Shield technology to protect our users against data theft, web injection, and other vulnerabilities. Why don’t more companies adopt such measures? Because it requires significant investment. While I can’t disclose exact costs, I can say it is the single highest security expense we incur. We don’t just pay lip service to protecting our customers; we actively invest in their safety.
Key Features:
- JavaScript Monitoring and Threat Detection:
Cloudflare Page Shield tracks all JavaScript executed in the browser, including third-party scripts, and alerts administrators about unauthorized changes. This ensures that malicious scripts targeting sensitive user data are identified and blocked. - Real-Time Threat Blocking:
By monitoring script behavior and enforcing positive blocking policies, Page Shield prevents unauthorized scripts from executing on end-user browsers. For example, if browser-based malware attempts to send data to a malicious third party, Page Shield blocks the connection. - Content Security Policies (CSPs):
Page Shield employs CSP headers to ensure that only vetted and pre-approved JavaScript libraries are loaded and executed by browsers. This drastically reduces the attack surface for threats like Magecart-style attacks
Even in cases where the vulnerability exists on a customer’s web browser rather than our website, Cloudflare Page Shield ensures that sensitive information is not transmitted to malicious third parties during their session on our site. This proactive approach helps mitigate risks that originate outside our direct control while maintaining robust client-side security standards.
But what if something does happen?
Yes, we have an impressive security stack. Some might call it overkill. Even so, as the saying goes “you don’t know what you don’t know”. So in the unlikely even that your information is compromised on our site, we’re proud to provide the Norton Shopping Guarantee.
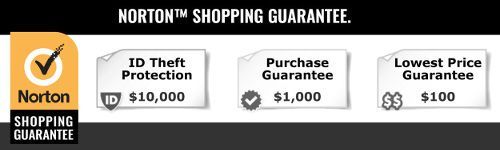
The presence of the Norton Shopping Guarantee seal indicates that this merchant’s identity, reputation, experience, financial stability, and ability to honor their sales terms and conditions have been inspected and verified. The merchant is monitored daily to ensure they always deliver on their terms of sale, thus assuring you a safe online shopping experience.
Key Features:
- $10,000 Identity Theft Protection – Provides up to $10,000 worth of specialist help & services in the event of identity theft for up to 30 days after your purchase.
- $1,000 Purchase Guarantee – A 30 day guarantee of up to a $1,000 of the purchase price, that you will receive the products/services you ordered, in accordance with the terms of sale.
- $100 Lowest Price Guarantee – If the store’s published price drops within 30 days of the purchase, you can make a claim for up to $100 of the difference.
How can I protect myself and my family?
- Keep your devices and software updated.
- Use a reputable malware / virus scanner on your devices.
- Don’t reuse passwords, ESPECIALLY not your email password. If someone gains access to your email, they can likely get into anything else.
- Protect your whole family with a DNS filter. We use DNSFilter.com.
- Protect your debit card information with Privacy.com. This allows you to generate many different “dummy credit card numbers” which you can use on specific websites.